Competing in the International Cyber Security Challenge 2023
In 2023, team Oceania consisted largely of returning players. This meant that having experienced last year’s podium struggle, those returning teammates were hungry for victory and out for blood. Although the competition only lasted two days, the effort Team Oceania put into not only practicing for the qualifiers, but also in preparations and training, spanned months leading up to the event.
This year’s competition consisted of a 6-hour Capture-the-flag (CTF) round followed by a 10 hour Attack/Defence (AD) round over two days. Unlike prior competitions we had the added excitement of an intense atmosphere fuelled by flashing lights, cameras and live DJ’s. To see for yourself there are livestreams of the event floating around various streaming platforms.
Preparation
Our success this year ultimately came from a huge, prolonged effort at developing custom team infrastructure and tooling. Several teammates voluntarily poured hours of their free time into this project, which was especially impressive considering most of them had to also work a full-time job. Some of these tools are expected to be released to the public soon on our team GitHub.
Competition Day 0: team Oceania vs unnamed airline
It turned out that the biggest challenge we faced was getting to the USA in the first place. With two cases of lost luggage and one cancelled flight (which was supposed to fly 4 of our 17 teammates out of Melbourne), it seemed like we had hit Airline Troubles Bingo. This ended up in the most unfortunate outcome, in which we had to leave a teammate behind. This left us with only 1 reserve, and an imbalance in skillset for the CTF round.
Competition Day 1: CTF
The CTF round was hosted by MetaCTF, whom some of us recognised as having also organised competitions for various other conferences, including BSides Melbourne. Being one player short, we all had plenty of anxiety going into the CTF round. One thing that lifted our hopes was that, compared to last year, this year’s CTF had many more hardware challenges. This played out nicely as it was an area some of us on the team are very good at. The rest of the challenges seemed to be pretty standard, with only 2 unconventional solutions.
Cheese
Most of us have experience writing CTF challenges (some for the largest CTF in Australia), and can sympathise with the organisers about grievances generated by a cheese solution. Luckily, the ones we discovered this year were more amusing than competition-throwing. One of the web challenges unintentionally leaked the flag file, which could be discovered with just a bit of fuzzing. The funniest of these incidents happened in the physical escape room, which we accidentally escaped by pulling a door off its magnets.
Competition Day 2: AD
The format of the attack/defence competition was very similar to last year’s, with the addition of a “King of the Hill” bot battle which seemed to fit more along the lines of a competitive programming competition than a traditional CTF. Although the game was designed to contain exploitable glitches and hacks, it quickly boiled down to strategy and programming ability. Some components of the game also required writing “assembly” code, somewhat reminiscent of a Zachtronics game.
The attack/defence round was definitely the more highly anticipated day for my team, as we would finally be putting all our custom infrastructure to the test. This accumulated into a nerve-wracking start to the competition, in which the blue team had to furiously scramble to deploy all the tools without losing too much uptime. In the red team, we joked that the ‘down’ in downunder stood for downtime, which in hindsight seems a bit cruel.
The livestream also featured this cool wizard graphic, which would show the successful attacks performed by each team in close to real time. Wizard-watching ended up being incorporated into our team’s strategy, after the scoreboard was frozen in the final hour.
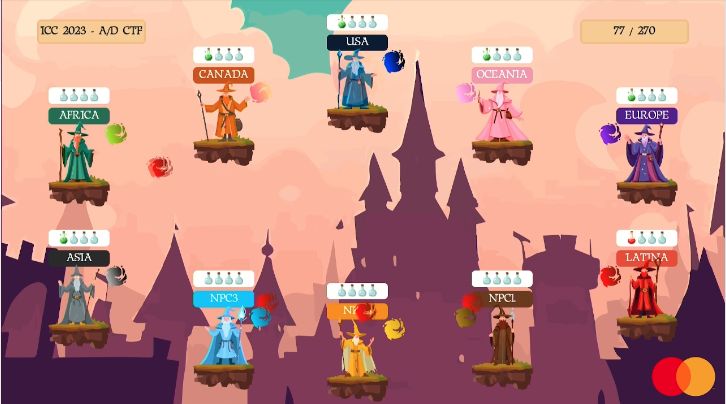
In the end, our hard work (and downtime) paid off when our defence tooling pulled us through the competition. This was crucial for us during the final hours of the day, when most teams had developed a strong set of exploits and were consistently attacking each other, but not us, giving us what looked to be an impenetrable defence against the other teams.
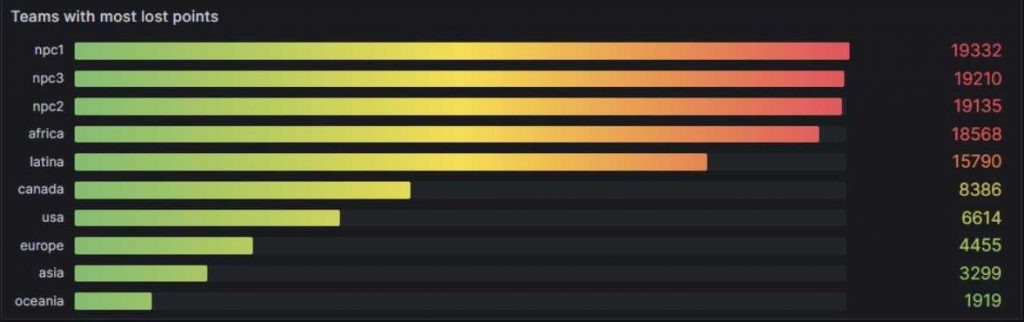
In the end, the organisers even told us that, had the competition continued for another half an hour, we would have scored in first place. Having missed out on third place by a hair’s breadth last year, we were absolutely stoked when we finally found out that we had won second place in this year’s ICCC.

Aftermath
After a successful result in San Diego, our team spirit was so strong it continued post-IC3 into DEFCON, which 15 out of 16 of our teammates ended up attending. Some of us even participated in various DEFCON competitions as team “OCE_IS_BEST”. Each time one of these groups were announced at the DECFON awards ceremony felt like a bonus victory for the team. Our team also contained one epsilon of a DEFCON CTF team, whose sizes have gotten so large they may as well all merge into one single team next year (so everyone can get that shiny black badge).
All this to say, if there’s anything to learn from CTFs, it’s that the real skills are truly the friends we make along the way.
- Written by: Chuanshu Jiang
- Posted on: September 5, 2023
- Tags: Competitions, ctf


